The security and integrity of computer networks are of paramount importance in today’s interconnected world, as they provide the backbone of communication and data transmission. Yet, cyber risks persist, and cybercriminals are perpetually on the lookout for novel entry points through which to breach networks. ARP spoofing is one method of attack since it may be used to intercept and alter network communication. Network administrators and security experts use ARP inspection as a powerful tool to counteract this threat. In this piece, we’ll investigate what ARP inspection is, why it’s important, and how it can protect networks from ARP spoofing attacks.
ARP Spoofing: What Is It?
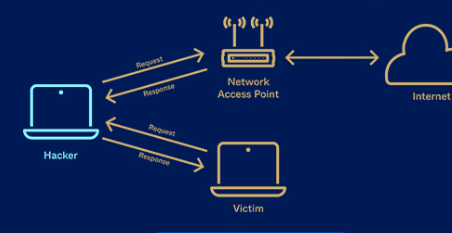
Let’s get familiar with ARP spoofing before diving into ARP examination. The Address Resolution mechanism (ARP) is a standard mechanism in LANs for translating IP addresses into physical network interface cards (MAC) addresses. In order for two devices on a network to exchange data, each must have the other’s media access control (MAC) address. It queries “Who has this IP address?” via an ARP request. After receiving its MAC address, the replying device continues the conversation.
The Address Resolution Protocol (ARP) can be maliciously manipulated by a technique known as ARP spoofing, sometimes known as ARP poisoning. The attacker in an ARP spoofing attack sends out bogus ARP answers, pretending to be the owner of the correct MAC address for a target IP. Thus, the victim’s network traffic is rerouted to the attacker’s machine, enabling the latter to monitor, alter, or even eavesdrop on the victim’s communications with other devices on the network. Man-in-the-middle attacks, session hijacking, and other forms of data theft are all possible outcomes of traffic interception.
Importance of ARP Testing
The effects of an ARP spoofing attack can be disastrous, from information loss to system outages. As a precaution against ARP spoofing, ARP inspection is a useful security measure. When combined with other security measures, such as DHCP snooping, it is commonly implemented at the switch level. In order to protect a network from malicious ARP spoofing efforts, ARP inspection keeps a close eye on and verifies every incoming and outgoing ARP packets.
ARP Inspection and Its Functions
In order to ensure that received ARP packets are legitimate, they must first undergo an ARP inspection. You may sum up the steps like this:
- Using valid DHCP transactions, DHCP snooping generates a binding database that maps IP addresses to their associated MAC addresses. The switch keeps track of this table so it can check it during an ARP probe.
- When a switch receives an ARP packet, it performs an inspection called ARP inspection, which verifies the packet by comparing the source IP address, source MAC address, and DHCP snooping binding table entries. If everything checks out, then the ARP packet can be trusted and processed further. The ARP packet is discarded if the data does not match or seems faked.
- In addition to traditional port security measures, ARP inspection can be performed. The detection of several MAC addresses on a single switch port can cause the port to be disabled or an alert to be sent to the network administrator.
Preventing Attacks Via ARP Spoofing
- By implementing ARP inspection, network security may be greatly improved and ARP spoofing attacks can be prevented. Key advantages of ARP inspection and how it aids in defending against this threat are as follows:
- ARP inspection is able to effectively thwart ARP spoofing efforts because it verifies the authenticity of ARP packets. In order to protect the network from infiltration, any suspicious ARP replies are immediately deleted.
- Increased Network Visibility Thanks to ARP inspection, you can learn what hardware is connected to each switch port. With this insight, admins can spot malicious devices or people trying to snoop on network data and shut them off.
- Network isolation and segmentation can be achieved by combining ARP inspection with other security techniques like VLAN isolation. This restricts the attackers’ ability to move laterally and mitigates the damage of any security holes.
- The attack surface of a network can be minimized through the use of ARP inspection, which can identify and counteract ARP spoofing attempts. This preventative measure lessens the likelihood that attackers will be able to take advantage of security holes in the network.
Guidelines for Conducting ARP Inspections
- Network administrators can improve the efficiency of ARP inspection by adhering to these guidelines.
- If you want to protect your network from ARP spoofing attacks, you should turn on ARP inspection for all network access points.
- Integrate ARP Inspection with Existing Security Measures: Port protection, DHCP snooping, and intrusion detection systems (IDS) are just a few examples of other security mechanisms that can complement ARP inspection and increase its effectiveness.
- Updating the DHCP snooping binding table on a regular basis ensures that the information used to validate ARP packets remains accurate.
- Keep an eye on ARP traffic and analyze it on a regular basis to spot any irregularities that could indicate ARP spoofing.
- It is important to inform network users of the dangers posed by ARP spoofing. The likelihood of falling prey to social engineering-based ARP spoofing attacks can be mitigated through increased education.
Conclusion
Since ARP spoofing attacks are a serious danger to network security, ARP inspection is crucial for protecting against them. By checking the integrity of ARP packets, ARP inspection helps prevent ARP spoofing attacks and strengthens the safety of the network as a whole. When building a defense against potential breaches, protecting sensitive data, and preserving the integrity of network connections, ARP inspection should be implemented as a top priority for network administrators and security specialists. Modern computer networks rely heavily on the confidence and reliability of its users, which must be protected with a proactive and watchful approach to network security.